If you are using the plugin Easy WP SMTP for sending site emails using SMTP, make sure that you update to version 1.3.9.1. Do not delay updating any of your child sites, as using the unfixed version of the plugin gives your child site a high chance of being hacked.

For more information about the critical zero-day vulnerability issue in Easy WP SMTP plugin, you can read this post. WPScan also has more information.
The hack will take the form of an admin user being created, due to a vulnerability in the older unpatched version of the plugin. The siteurl will then be changed to an external site. This means that user permissions might be changed, and the site will not load correctly when the siteurl value is not correct.
If you need a short-term fix to be able to get into a wp-admin of the site which was hacked, you can define home and siteurl in the child sites wp-config.php file.
define( 'WP_HOME', 'https://sitedomain.com' ); define( 'WP_SITEURL', 'https://sitedomain.com' );
Once you have got into wp-admin of the site and changed siteurl and home from Settings > General.

Then you can remove the constants for siteurl and home set in the child sites wp-config.php file.
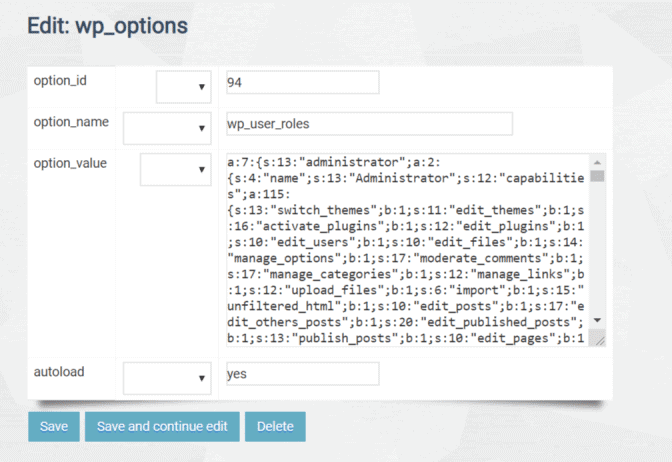
If you can access phpMyAdmin, select the site’s options database table. In the siteurl option value, change the URL back to match the correct site URL, and save the change.

To correct the hack, look for any admin users which did not exist previously. Also, look for any users who have had permissions changed. Also, look that the permissions in the wp_user_roles option name is set correctly. Since this could mean that all users on the site, including subscribers, have admin permissions. If you have a recent backup before the hack, restore from that backup, then make sure that the Easy WP SMTP plugin is updated to the most current version after the site has been restored.

It is also recommended that you can run a scan on the child site, to make sure that nothing else has been changed on the site, two recommended plugins would be NinjaScanner – Virus & Malware scan or Anti-Malware Security and Brute-Force Firewall.

Worth also looking into using the Activity Log for MainWP extension, so that all child site changes are being tracked using the WP Security Audit Log plugin.
It may also be worth looking into moving away from using any SMTP based plugins and going with a dedicated transactional email provider, ones to look at would be SendGrid, SparkPost and Postmark.
By keeping child sites plugins updated at all times and staying up to date on newer plugins, you can prevent hacks and security breaches, which will keep you and your clients happy.






1 thought on “Easy WP SMTP Plugin Vulnerability Update Immediately”
Additional steps for hacked site cleanup included in this support post from WordPress.org.
https://wordpress.org/support/topic/the-fix-to-get-back-in-to-infected-site/
Comments are closed.